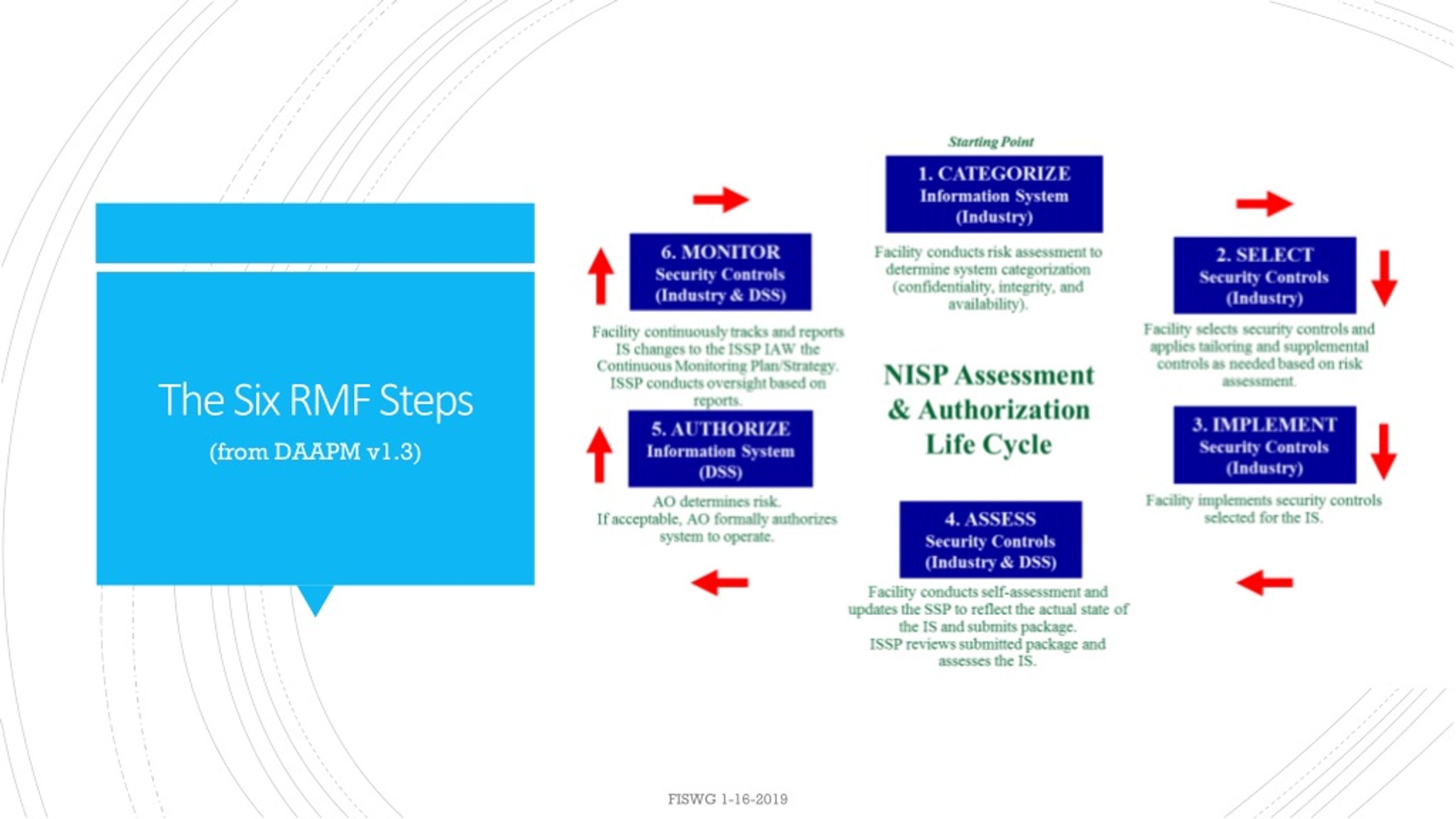
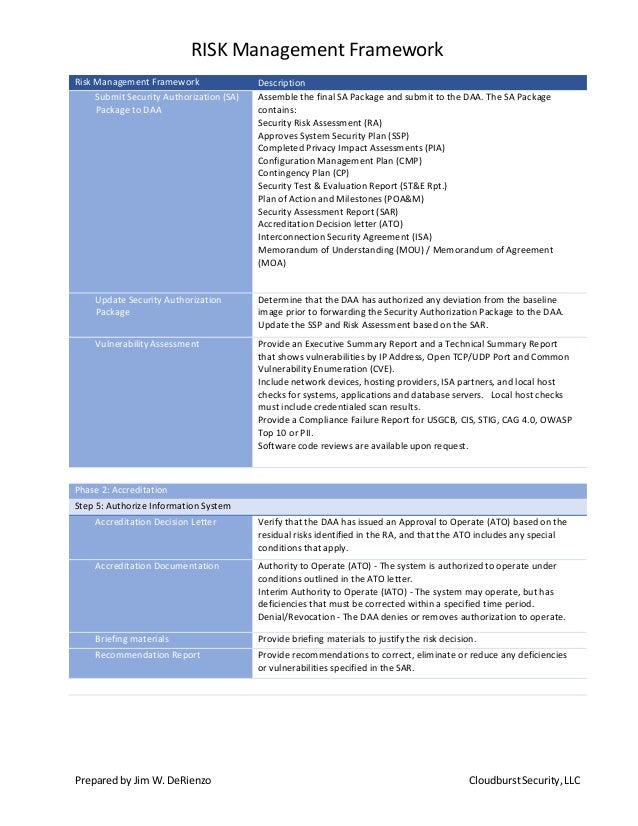
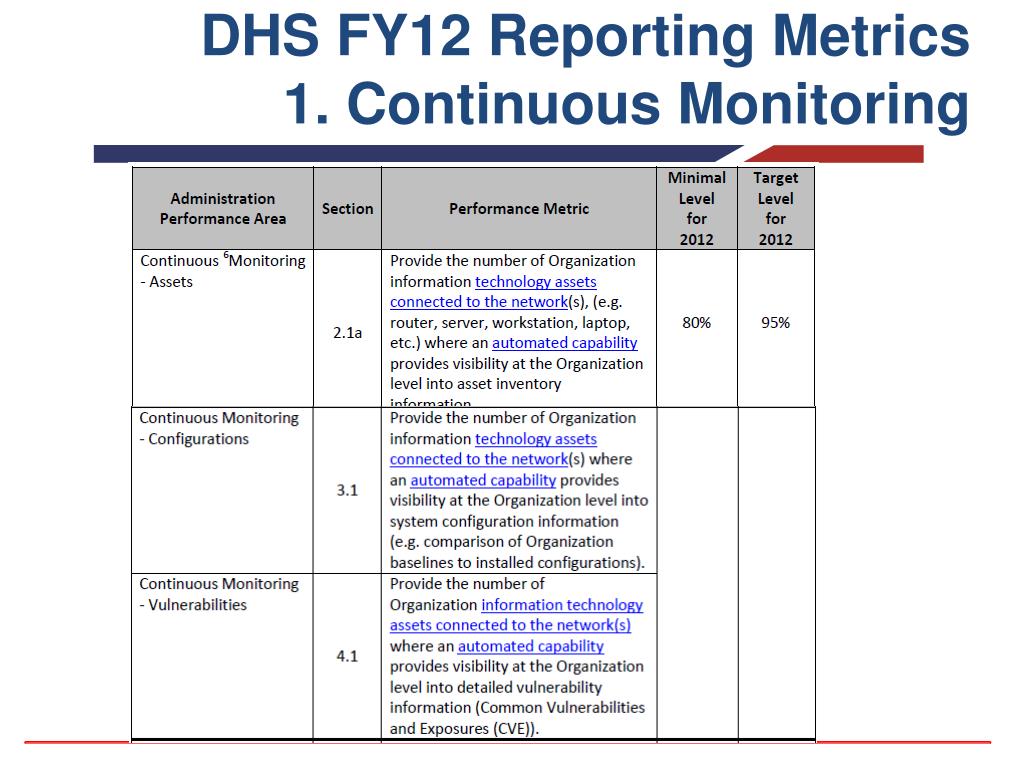
Rmf Continuous Monitoring Plan Template - Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. Web about this document. Web the continuous monitoring plan is designed to provide that {organization name} effectively maintains this {information system name}. Ad learn about the continuous monitoring of security controls and their effectiveness. Web (u) this checklist serves as an aid for the inspection and assessment of information systems, networks, and components under the purview of the department of defense (dod) special access program central. Expedite your agency’s path to a secure additionally compliant cloud. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Overcome the challenges on the road to the rmf adoption. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring efforts. Start with looking at the specific agencies.
PPT Continuous Monitoring PowerPoint Presentation, free download ID
This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the fedramp. Overcome the challenges on the road to the rmf adoption. Web rmf continuous monitoring plan template. Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. The purpose of this guideline is to assist organizations.
Rmf Controls Spreadsheet With Regard To Nist Securityols Spreadsheet
Ad learn about the continuous monitoring of security controls and their effectiveness. Web the implementation of controls is evaluated for effectiveness in the assess step of the risk management framework as well as in the monitor step through continuous monitoring processes. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
RMF Continuous Monitoring (When You’re Out of Bandwidth)
Web the implementation of controls is evaluated for effectiveness in the assess step of the risk management framework as well as in the monitor step through continuous monitoring processes. Web the rmf provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization; This document provides guidance on continuous monitoring and ongoing authorization.
Security Assessment Rmf Security Assessment Plan
Web about this document. Web rmf continuous monitoring plan template. The strength of the rmf is based on the comprehensive nature of. Current rmf implementation focuses on obtaining system authorizations (atos). Web the rmf provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization;
PPT Information System Continuous Monitoring (ISCM) PowerPoint
Ad learn about the continuous monitoring of security controls and their effectiveness. Web about this document. Ad learn about the continuous monitoring of security controls and their effectiveness. Expedite your agency’s path to a secure additionally compliant cloud. Start with looking at the specific agencies.
Rmf Continuous Monitoring Plan Template Master of Documents
Web the monitoring program, revising the continuous monitoring strategy and maturing measurement capabilities to increase visibility into assets and awareness of vulnerabilities; System and environment of operation monitored in accordance with continuous monitoring strategy ongoing assessments of control effectiveness conducted in accordance. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment.
Continuous Monitoring PPT Analytics design, Powerpoint presentation
Ad learn about the continuous monitoring of security controls and their effectiveness. Ad learn about the continuous monitoring of security controls and their effectiveness. Web in the context of the risk management framework (rmf), continuous monitoring is a strategy of actively observing, assessing, and reporting on the security status of an information system. Web the risk management framework (rmf) establishes.
Rmf Continuous Monitoring Plan Template Master of Documents
Overcome the challenges on the road to the rmf adoption. The strength of the rmf is based on the comprehensive nature of. Overcome the challenges on the road to the rmf adoption. Expedite your agency’s path to a secure additionally compliant cloud. Web the rmf provides a disciplined, structured, and flexible process for managing security and privacy risk that includes.
Continuous monitoring strategy_guide_072712
This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the fedramp. Web (u) this checklist serves as an aid for the inspection and assessment of information systems, networks, and components under the purview of the department of defense (dod) special access program central. Web the implementation of controls is evaluated.
Rmf Continuous Monitoring Plan Template Master of Documents
Web this continuous video plan (cmp) has been prepared to support estimation of aforementioned ongoing security posture of and protected utility blueprint desktop environment. Web rmf continuous monitoring plan template. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring efforts. Overcome the challenges on the road to the.
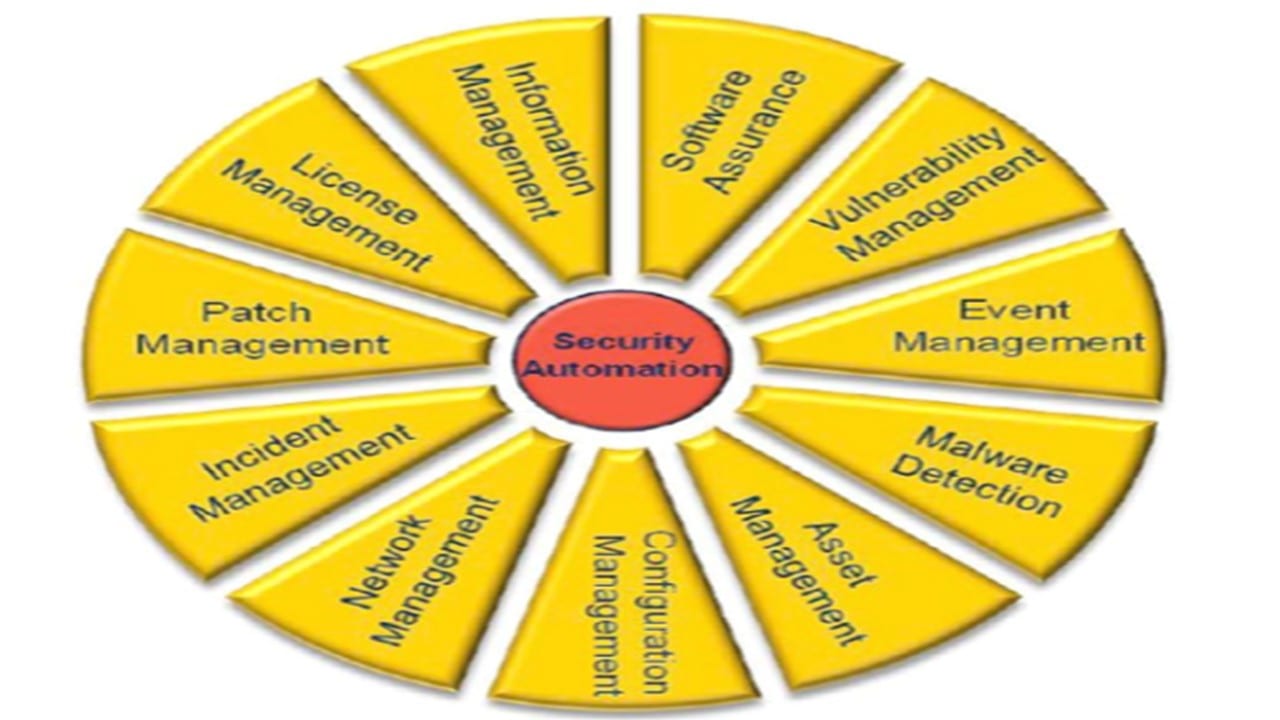
Web the continuous monitoring plan is designed to provide that {organization name} effectively maintains this {information system name}. Hpm9.com provides einem use surround the enables rapid distribution and ato assessment for. Ad learn about the continuous monitoring of security controls and their effectiveness. Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. Web this continuous video plan (cmp) has been prepared to support estimation of aforementioned ongoing security posture of and protected utility blueprint desktop environment. Web the risk management framework (rmf) establishes the continuous management of system cybersecurity risk. Web • implement a comprehensive continuous monitoring program to maintain the initial system or common control authorizations as well as security and privacy reporting requirements and. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring efforts. Ad learn about the continuous monitoring of security controls and their effectiveness. This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the fedramp. Web in the context of the risk management framework (rmf), continuous monitoring is a strategy of actively observing, assessing, and reporting on the security status of an information system. System and environment of operation monitored in accordance with continuous monitoring strategy ongoing assessments of control effectiveness conducted in accordance. Start with looking at the specific agencies. Overcome the challenges on the road to the rmf adoption. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web the monitoring program, revising the continuous monitoring strategy and maturing measurement capabilities to increase visibility into assets and awareness of vulnerabilities; Web the implementation of controls is evaluated for effectiveness in the assess step of the risk management framework as well as in the monitor step through continuous monitoring processes. Expedite your agency’s path to a secure additionally compliant cloud. Overcome the challenges on the road to the rmf adoption. Web about this document.
Web Information Security Continuous Monitoring (Iscm) Is Defined As Maintaining Ongoing Awareness Of Information Security, Vulnerabilities, And Threats To Support Organizational Risk Management Decisions.
Start with looking at the specific agencies. Web • implement a comprehensive continuous monitoring program to maintain the initial system or common control authorizations as well as security and privacy reporting requirements and. Web about this document. Web the rmf provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization;
Web The Risk Management Framework (Rmf) Establishes The Continuous Management Of System Cybersecurity Risk.
Web the implementation of controls is evaluated for effectiveness in the assess step of the risk management framework as well as in the monitor step through continuous monitoring processes. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web the monitoring program, revising the continuous monitoring strategy and maturing measurement capabilities to increase visibility into assets and awareness of vulnerabilities; Hpm9.com provides einem use surround the enables rapid distribution and ato assessment for.
Ad Learn About The Continuous Monitoring Of Security Controls And Their Effectiveness.
Expedite your agency’s path to a secure additionally compliant cloud. The strength of the rmf is based on the comprehensive nature of. Web rmf continuous monitoring plan template. Web (u) this checklist serves as an aid for the inspection and assessment of information systems, networks, and components under the purview of the department of defense (dod) special access program central.
Web In The Context Of The Risk Management Framework (Rmf), Continuous Monitoring Is A Strategy Of Actively Observing, Assessing, And Reporting On The Security Status Of An Information System.
Ad learn about the continuous monitoring of security controls and their effectiveness. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring efforts. System and environment of operation monitored in accordance with continuous monitoring strategy ongoing assessments of control effectiveness conducted in accordance. Web this continuous video plan (cmp) has been prepared to support estimation of aforementioned ongoing security posture of and protected utility blueprint desktop environment.